Getting Covenant Payloads past Windows Defender [outdated]
Introduction
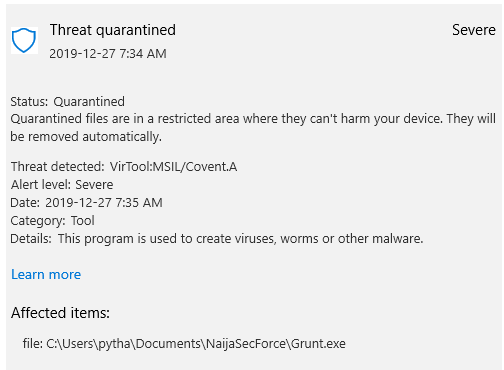
I wrote an article about a month ago about Covenant and Donut, and mentioned that to get your Covenant payloads past AVs, all you have to do is rename keywords like "Grunt", "Stager" and "Covenant". However, this technique is no longer effective against Defender as a recent binary payload I altered the same way was immediately detected and quarantined. This shows how fast things change within the offensive and defensive cyber space.In this post, I will show a little trick to modify a grunt payload (C#) and get it past Defender (thus, 98% of other AVs). By default, an unmodified payload is detected as VirTool:MSIL/Covent.A. Part of the alert name "Covent" indicates Defender knows that this payload is from the Covenant C2.
A snippet of the alert is shown below:
Looking through the C# code, I modified a lot more keywords that seems to be uniquely associated with Covenant, but this didn't do much as the same alert was thrown anytime the code is recompiled.
For a quick minute, I thought this might be due to the fact that I wasn't using a certificate to encrypt traffic but the scan was not a dynamic one but static, hence it had nothing to do SSL or traffic encryption. Anyways, I started renaming or removing certain lines I thought would trigger such alert, that was when I noticed "MessageFormat" variable shown in line 54.
This variable defines the format of the HTTP request that will be sent to the C2 server, and the request message has to be in that format, else the server will not understand the request and there won't be a "reverse shell". When I modified this line to something random as shown below (line 54), Defender didn't see it as a threat.
Defender Scan:
So there is a need to re-write the same line in a different way without using the same keywords and pattern in order to avoid static scanning. A simple way to do this was to use the base64 encoded version of the MessageFormat variable in the following way:
1. Get the encoded version
2. Replace the MessageFormat variable with the base64 encoded version
3. Use another string variable to store the decoded version and continue execution.
To get the encoded version of the variable, I executed the following code:
The encoded form was then used in the covenant C# payload as shown below:
Upon compilation, it was no longer flagged as a threat and I got my "reverse shell". You can also use this with donut, get shellcode and inject into processes.








Comments
Post a Comment