Getting Covenant Payloads past Windows Defender [outdated]
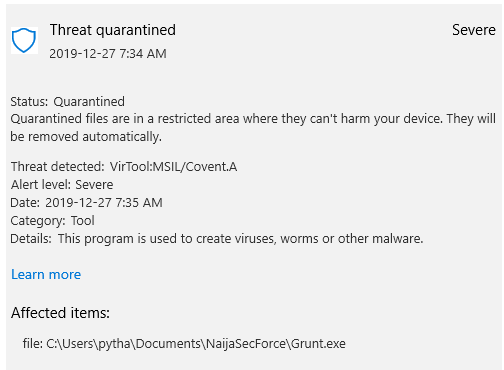
Introduction I wrote an article about a month ago about Covenant and Donut , and mentioned that to get your Covenant payloads past AVs, all you have to do is rename keywords like "Grunt", "Stager" and "Covenant". However, this technique is no longer effective against Defender as a recent binary payload I altered the same way was immediately detected and quarantined. This shows how fast things change within the offensive and defensive cyber space. In this post, I will show a little trick to modify a grunt payload (C#) and get it past Defender (thus, 98% of other AVs). By default, an unmodified payload is detected as VirTool:MSIL/Covent.A . Part of the alert name " Covent " indicates Defender knows that this payload is from the Covenant C2. A snippet of the alert is shown below: Looking through the C# code, I modified a lot more keywords that seems to be uniquely associated with Covenant, but this didn't do much as the same alert wa...

