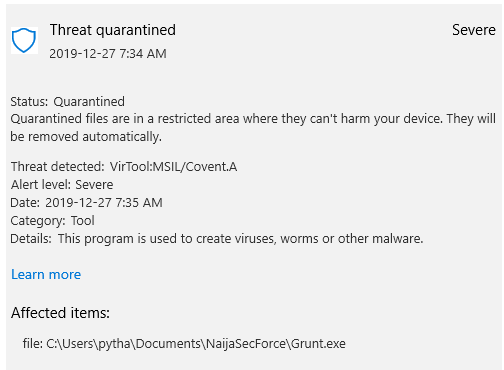
Covenant Task 101 - PPID Spoof Example
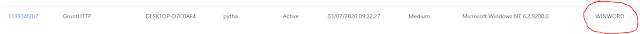
Covenant is a great C2 tool for red teaming. I use it on most engagements as its in C# and easily extensible. This post was inspired by Rasta Mouse's Covenant 101 where he nicely described how to modify Covenant source to add a task. The purpose of this post is to leverage Rasta's post to further simplify the process especially for those new to Covenant. Ryan Cobbr, the main author of Covenant has already done a great job by adding a "Tasks" menu where an admin user can lists all tasks and modify their configurations. I will be be showing how I leveraged this in a recent engagement to bypass certain EDRs and AV behavioural signatures. Story Time Once upon a time, I was contracted to do a red teaming engagement for one of the World's leading pharmaceutical firms. Fast forward to when I crafted and had sent a neat phishing mail (embedded with a link to a malicious Word doc). Within 10 mins, about 9 users had clicked, and I had 9 grunts, however, the grunts we...